The latest version of 500-220 dumps released today, proven, correct, and effective, candidates can use the PDF and VCE exam tools provided by Lead4Pass to help you practice all exam questions, guaranteeing you 100% success in passing the Cisco 500-220 ECMS exam (Engineering Cisco Meraki Solutions).
All candidates taking the Cisco 500-220 ECMS exam can download the latest version of the 500-220 dumps online: https://www.leads4pass.com/500-220.html. And take advantage of the discount code “Cisco” for the lowest price on the Internet “.
The latest Cisco 500-220 Dumps exam questions are shared online:
| Number of exam questions | Update time | Exam | Previous issue |
| 15 | Sep 13, 2022 | Cisco Meraki Solutions Specialist (500-220) | Apr 26, 2022 |
Question 1:
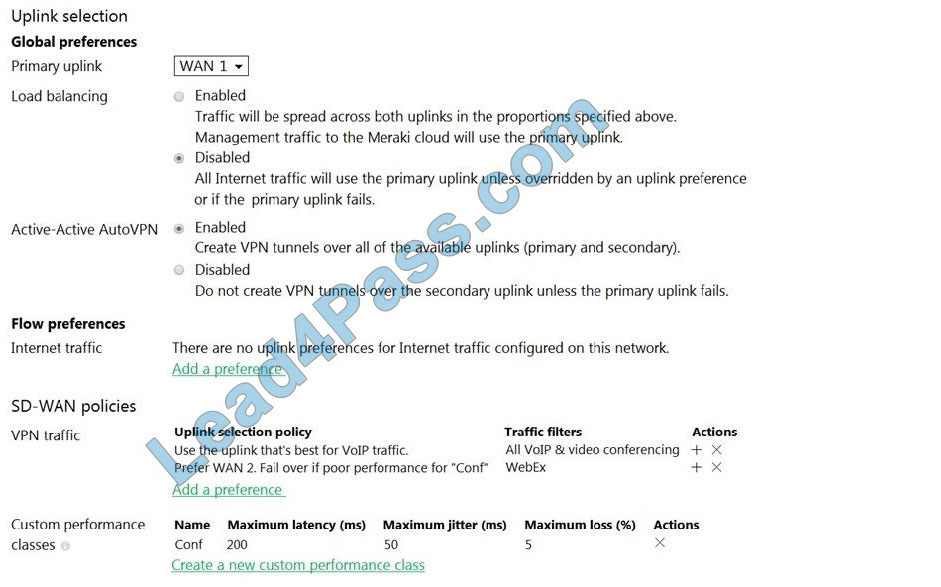
Refer to the exhibit. Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?
A. WebEx traffic will prefer WAN 2 as long as it meets the thresholds in the “Conf” performance class.
B. WebEx traffic will prefer WAN 1 as it is the primary uplink.
C. WebEx traffic will prefer WAN 2 as long as it is up.
D. WebEx traffic will be load-balanced between both active WAN links.
Question 2:
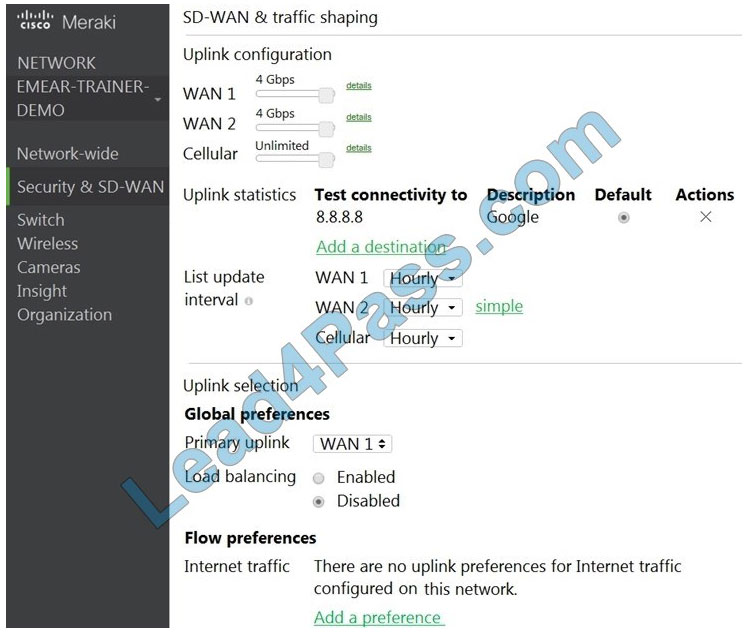
Refer to the exhibit. Which two actions are required to optimize load balancing asymmetrically with a 4:1 ratio between links? (Choose two.)
A. Change the primary uplink to “none”.
B. Add an internet traffic preference that defines the load-balancing ratio as 4:1.
C. Enable load balancing.
D. Set the speed of the cellular uplink to zero.
E. Change the assigned speeds of WAN 1 and WAN 2 so that the ratio is 4:1.
Question 3:
Which Cisco Meraki best practice method preserves complete historical network event logs?
A. Configuring the preserved event number to maximize logging.
B. Configuring the preserved event period to unlimited.
C. Configuring a Syslog server for the network.
D. Configuring Dashboard logging to preserve only certain event types.
Question 4:
Which design requirement is met by implementing Syslog versus SNMP?
A. when automation capabilities are needed
B. when proactive alerts for critical events must be generated
C. when organization-wide information must be collected
D. when information such as flows and client connectivity must be gathered
Question 5:
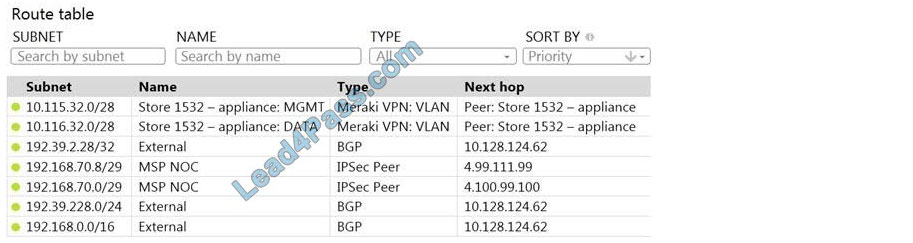
Refer to the exhibit. A packet arrives on the VPN concentrator with source IP 10.168.70.3 and is destined for IP 10.116.32.4. What is the next hop for the packet, based on this concentrator routing table?
A. The concentrator gateway (10.128.124.62) is the next hop.
B. Not enough detail is available to determine the next hop.
C. The packet is stopped.
D. The Auto VPN peer “Store 1532 ? appliance” is the next hop.
Question 6:
Company iPads are enrolled in Systems Manager without supervision, and profiles are pushed through Systems Manager. Which outcome occurs when a user attempts to remove the “Meraki Management” profile on an iPad?
A. The “Meraki Management” profile cannot be removed.
B. The “Meraki Management” profile is removed and then pushed automatically by the Systems Manager.
C. The “Meraki Management” profile is removed. All the profiles that Systems Manager pushed are also removed.
D. The “Meraki Management” profile is removed. All the profiles Systems Manager pushed remain.
Question 7:
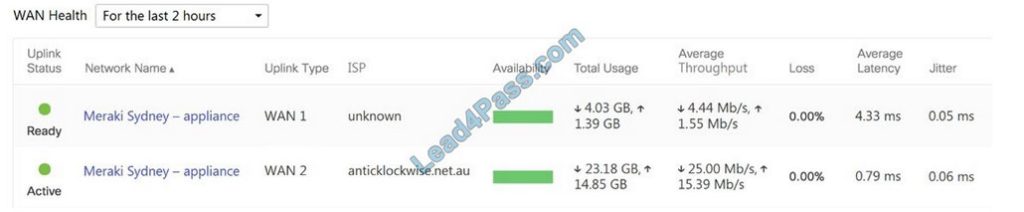
Refer to the exhibit. What are the Loss and Average Latency statistics based on?
A. responses that the MX appliance receives on the connectivity-testing hostnames on the Insight > Web App Health page
B. responses that the MX appliance receives on the connectivity-testing IP addresses on the Security and SD-WAN > Firewall page
C. responses that the MX appliance receives on the connectivity-testing IP address that is configured on the Security and SD-WAN > SD-WAN and Traffic Shaping page
D. responses that the MX appliance receives on the connectivity-testing IP addresses on the Help > Firewall info page
Question 8:
In an organization that uses the Co-Termination licensing model, which two operations enable licenses to be applied? (Choose two.)
A. Renew the Dashboard license.
B. License a network.
C. License more devices.
D. Call Meraki support.
E. Wait for the devices to auto-renew.
Question 9:
What are two ways peers interact with ports that Auto VPN uses? (Choose two.)
A. For IPsec tunneling, peers use high UDP ports within the 32768 to 61000 range.
B. Peers contact the VPN registry at UDP port 9350.
C. For IPsec tunneling, peers use high TCP ports within the 32768 to 61000 range.
D. Peers contact the VPN registry at TCP port 9350.
E. For IPsec tunneling, peers use UDP ports 500 and 4500.
Question 10:
What occurs when a configuration change is made to an MX network that is bound to a configuration template?
A. The configuration change in the bound network is combined with the template configuration inside the template.
B. The more restrictive configuration is preferred.
C. The configuration change in the bound network overrides the template configuration.
D. The template configuration overrides the configuration change in the bound network.
Question 11:
One thousand concurrent users stream video to their laptops. A 30/70 split between 2.4 GHz and 5 GHz is used. Based on client count, how many APs (rounded to the nearest whole number) are needed?
A. 26
B. 28
C. 30
D. 32
Question 12:

Refer to the exhibit. For an AP that displays this alert, which network access control method must be in use?
A. preshared key
B. WPA2-enterprise with my RADIUS server
C. splash page with my RADIUS server
D. MAC-based access control with RADIUS server
Question 13:
Which Meraki Dashboard menu section is accessed to enable Sentry enrollment on an SSID?
A. Wireless > Configure > Access Control
B. Wireless > Configure > Splash page
C. Wireless > Configure > Firewall and Traffic Shaping
D. Wireless > Configure > SSIDs
Question 14:
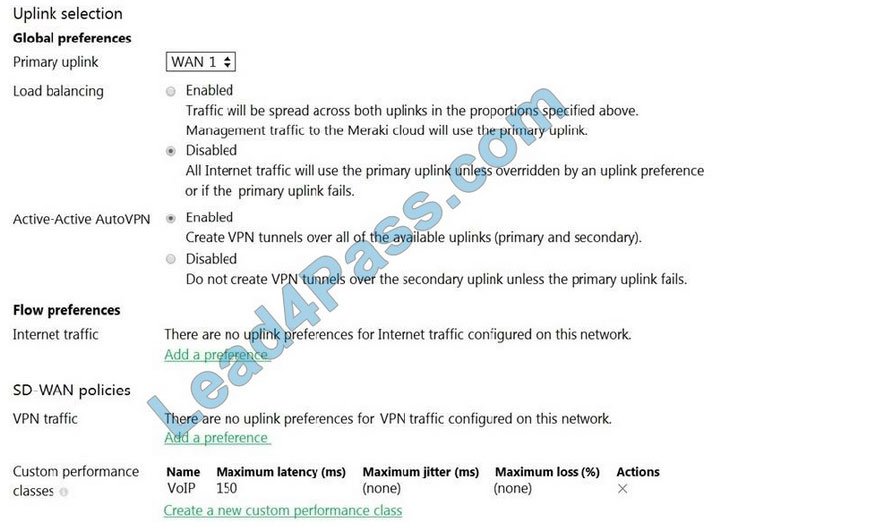
Refer to the exhibit. What does the MX Security Appliance send to determine whether VPN traffic exceeds the configured latency threshold in the VoIP custom performance class?
A. 1000-byte TCP probes every second, through VPN tunnels that are established over the primary WAN link.
B. 100-byte UDP probes every second, through VPN tunnels that are established over every WAN link.
C. 100-byte UDP probes every second, through VPN tunnels that are established over the primary WAN link.
D. 1000-byte TCP probes every second, through VPN tunnels that are established over every WAN link.
Question 15:
What is the role of the Meraki Dashboard as the service provider when using SAML for single sign-on to the Dashboard?
A. The Dashboard generates the SAML request.
B. The Dashboard provides user access credentials.
C. The Dashboard parses the SAML request and authenticates users.
D. The Dashboard generates the SAML response.
Verify the answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | B | BC | A | D | B | C | B | AC | BC | A | C | A | A | D | A |
The above Cisco 500-220 Dumps exam contains 15 questions that you can practice to improve yourself. The latest version of the 500-220 dumps, updated in September 2022, contains 57 exam questions and answers that candidates can practice to help them successfully pass Cisco 500-220 ECMS exam. You are welcome to use the latest version of 500-220 dumps https://www.leads4pass.com/500-220.html. Escort your career leap.
