Candidates use the latest updated DevNet Associate 200-901 dumps from Lead4Pass 2023: https://www.leads4pass.com/200-901.html to help them jump over the hurdles and pass the 200-901 DEVASC exam successfully.
Lead4Pass 200-901 dumps provide PDF files and a VCE exam engine to help you practice 200-901 DEVASC exam questions quickly and easily. The latest updated 200-901 dumps contain 437 exam questions and answers, verified by IT experts to be true and effective.
Read DevNet Associate 200-901 Dumps Exam Questions and Answers Shared Free 2023 Online:
| Type | Number of exam questions | Exam name | Exam code | Last updated |
| Free | 15 | Developing Applications and Automating Workflows using Cisco Platforms (DEVASC) | 200-901 | 200-901 dumps |
Question 1:
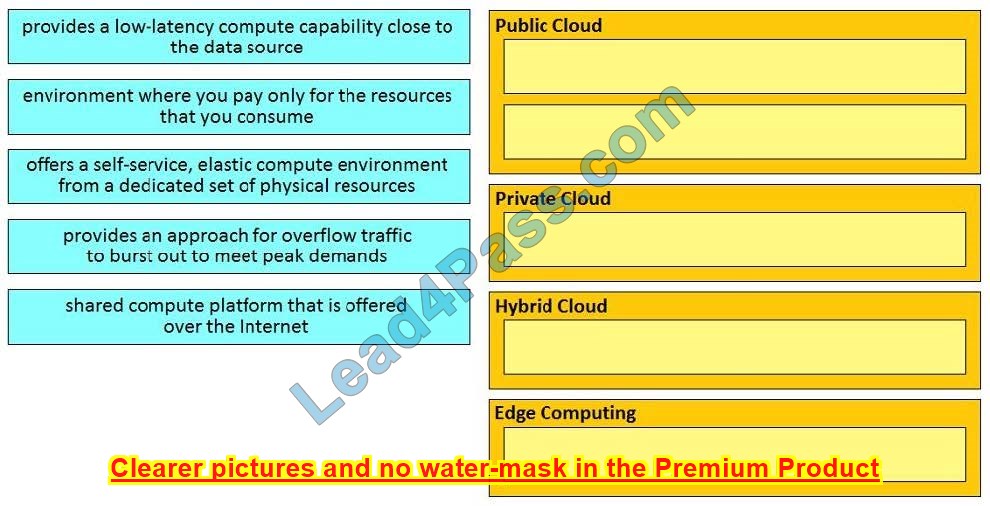
DRAG DROP
Drag and drop the HTTP status codes from the left onto the correct descriptions on the right.
Select and Place:

Correct Answer:
Question 2:
What is a principle of a code review process?
A. Changes are made after the code is submitted to source control.
B. It must not prevent code from getting into production as quickly as possible.
C. Naming standards must be consistent.
D. A technical lead must sign off on the review.
Correct Answer: D
Question 3:
A developer creates a web application that receives a username and password and uses them to sync the credentials to other services through HTTPS. API keys to services are part of the configuration files of the application, but the credentials to the database that stores the synchronization logs are obtained through an external vault service. What is the security issue in this scenario?
A. Communication between the application and the services is not encrypted.
B. The database credentials should be stored in the configuration files so that they are secured on the same server.
C. The API keys are stored in the configuration files but should be stored in the vault service.
D. The synchronization logs should be encrypted and not stored in a relational database.
Correct Answer: A
Question 4:
What are the two benefits of implementing common data structures when working with APIs in remote systems? (Choose two.)
A. ensures that developers are limited to using one data schema type
B. prevents multivendor interoperability
C. improves security in RESTful web services
D. enforces standardized data structures
E. leverages code that is easily managed and reused
Correct Answer: BE
Question 5:
A developer creates a script that configured multiple Cisco IOS XE devices in a corporate infrastructure. The internal test environment is unavailable, and no maintenance window is available to test on a low-priority production environment. Which resource is used to test the code before it is applied to the production environment?
A. Code Exchange
B. Cisco DevNet Learning Labs
C. Cisco DevNet Sandbox
D. Cisco Support
Correct Answer: C
Question 6:
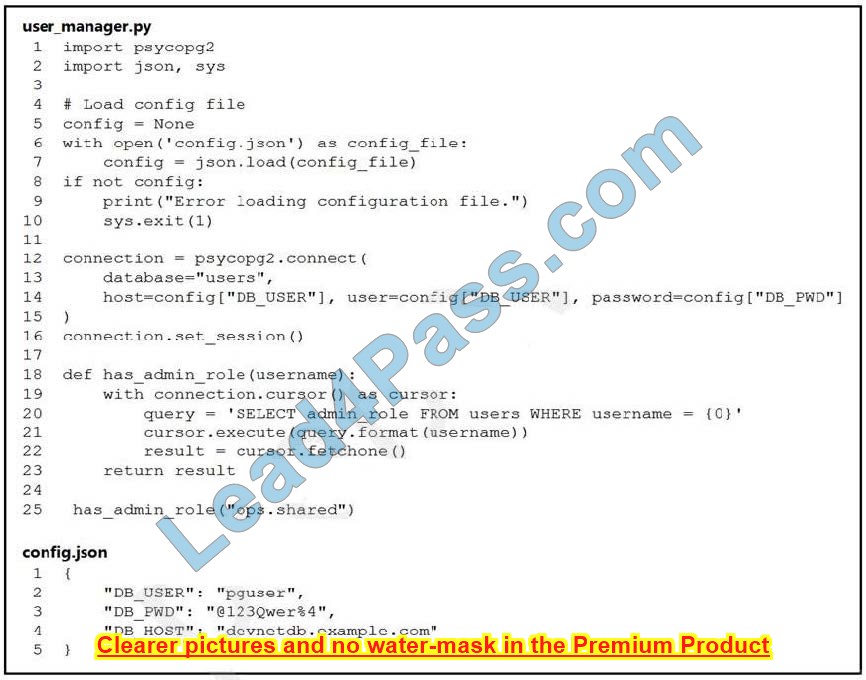
Refer to the exhibit. An engineer must check the admin rights of users on a database regularly and prepares the Python script to automate the process. The script connects to the database and runs a query. What is a security issue about the secrets in the code that relates to secret protection?
A. They must be stored in configuration files if there is a possibility of leakage.
B. They must be Base64-encoded if stored in the user database.
C. They must be encrypted if stored in the user database.
D. They must be stored in configuration files if no authentication will be used.
Correct Answer: D
Question 7:
Which advantage does the agile process offer compared to waterfall software development?
A. to add or update features with incremental delivery
B. to view the full scope of end-to-end work
C. to have each phase end before the next begins
D. to fix any issues at the end of the development cycle
Correct Answer: A
Question 8:
Which two statements are true about Cisco UCS Manager, Cisco UCS Director, or Cisco Intersight APIs? (Choose two.)
A. UCS Manager uses JSON to encode API interactions and utilizes Base64-encoded credentials in the HTTP header for authentication.
B. UCS Director API interactions can be XML- or JSON-encoded and require an API key in the HTTP header for authentication.
C. Cisco Intersight uses XML to encode API interactions and requires an API key pair for authentication.
D. UCS Manager API interactions are XML-encoded and require a cookie in the method for authentication.
E. Cisco Intersight API interactions can be encoded in XML or JSON and require an API key in the HTTP header for authentication.
Correct Answer: BD
Reference:
https://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/sw/api/b_ucs_api_book.pdf
Question 9:
Refer to the exhibit.
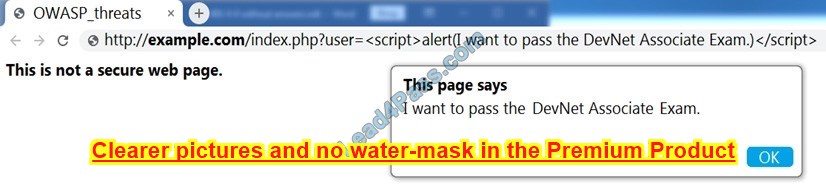
Which OWASP threat does this example demonstrate?
A. broken access control
B. cross-site scripting
C. SQL injection
D. man-in-the-middle
Correct Answer: B
Question 10:
Refer to the exhibit.
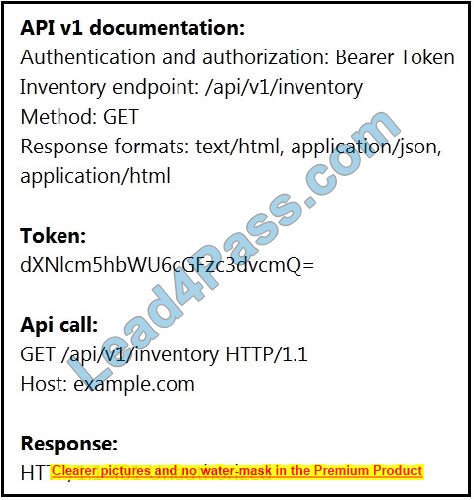
An API call is constructed to retrieve the inventory in XML format by using the API. The response to the call is 401 Unauthorized. Which two headers must he add to the API call? (Choose two.)
A. Bearer-Token: dXNlcm5hbWU6cGFzc3dvemQ=
B. Content-Type: application/XML
C. Authentication: Bearer dXNlcm5hbWU6cGFzc3dvemQ=
D. Accept: application/XML
E. Authorization: Bearer dXNlcm5hbWU6cGFzc3dvemQ=
Correct Answer: BE
Question 11:
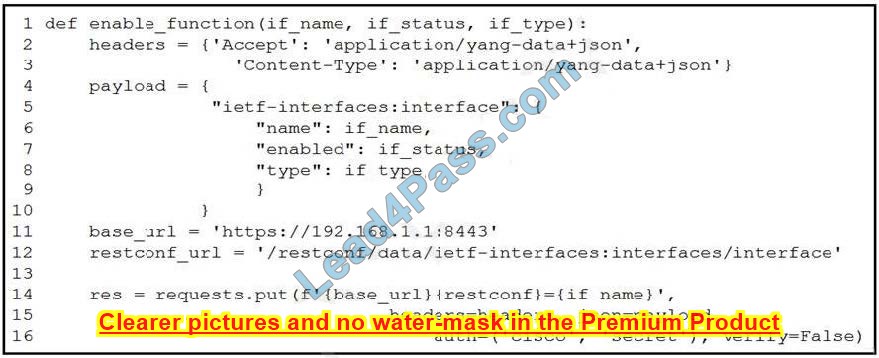
Refer to the exhibit. A network engineer wants to automate the port enable/disable process on specific Cisco switches. The engineer creates a script to send a request through RESTCONF and uses ietf as the YANG model and JSON as payload. Which command enables an interface named Loopback1?
A. enable_function(Loopback1, true, `iana-if-type:softwareLoopback\’)
B. enable_function(`iana-if-type:softwareLoopback\’, Loopback1, true,)
C. def enable_function(`iana-if-type:softwareLoopback\’, Loopback1, false,)
D. def enable_function(Loopback1, true, `iana-if-type:softwareLoopback\’)
Correct Answer: D
Question 12:
The developer is working on a new feature and made changes on a branch named ‘branch-413667549a-new’. When merging the branch to production, conflicts occurred. Which Git command must the developer use to recreate the pre-merge state?
A. git merge –no-edit
B. git merge –commit
C. git merge –revert
D. git merge –abort
Correct Answer: D
Question 13:
Which device is a system that monitors and controls the incoming and outgoing network traffic based on predetermined security roles?
A. router
B. switch
C. load balancer
D. firewall
Correct Answer: D
Question 14:
Refer to the exhibit.
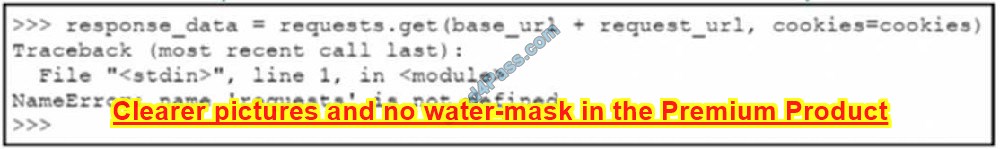
Python code has been written to query a device. The executed code results in the error shown. Which action resolves the problem?
A. import json
B. requests(“GET”, base_url + request_url, cookles=cookies)
C. pip install requests
D. import requests
Correct Answer: D
Question 15:
A developer completed the creation of a script using Git. Before delivering it to the customer, the developer wants to be sure about all untracked files, without losing any information. Which command gathers this information?
A. git clean –n
B. git rm –f
C. git clean –r
D. git rm *
Correct Answer: A
…
Candidates studying the DevNet Associate 200-901 dumps exam questions above can help improve their exam experience, but this is only a warm-up.
You are welcome to download the latest updated 2023 200-901 dumps: https://www.leads4pass.com/200-901.html, A truly effective route for candidates to pass the 200-901 DEVASC exam.
